Computer Incident Report Template. Collect data the best way with a flexible data collection device. Providing probably the most correct and factual info is the topmost accountability of the reporter. PDF model Generator likewise makes reports from order line. Please refrain from together with PII or SPII in incident submissions unless the data is necessary to understanding the character of the cybersecurity incident.
Most enterprise house owners and managers do this by creating a piece incident report. When Harvey fell, his colleague, Nick, who is about to enter the warehouse, heard a close-by bang that urges him to examine what happened. Finally, on the end, I stroll by way of the template and provides details about why each question is asked and the kind of solutions you must present.
According to W3Techs, four.4% of the highest 10 million websites use Shopify. Like your restore course of makes use of a DVD but your servers don’t have DVD drives. These incident templates can be found in PDF, Word, and Excel codecs for download. The incident response coverage ought to have an escalation record so that the correct people are engaged. As a outcome, the script removed a lot of products from the item_datafeed table that contains the URLs that lead to retailers’ online stores.
IT groups should then have the power to access, edit, and take action based on these preliminary reviews. We’ve supplied the most common fields for efficient incident reports. These embody descriptive components, as well as categorization fields and taxonomies.

This section gives recommendation to posture shopper to be more prepared and trained for subsequent laptop security incident. We investigate some host-based, network-based and procedural countermeasures are given to clients to cut back or get rid of risk of incident security. There have to be a set sample that’s different and it varies in each group when to quote a report or any query on any happening in the surrounding or has just happened.
Why Dont We Just Shut Down All Compromised Systems?
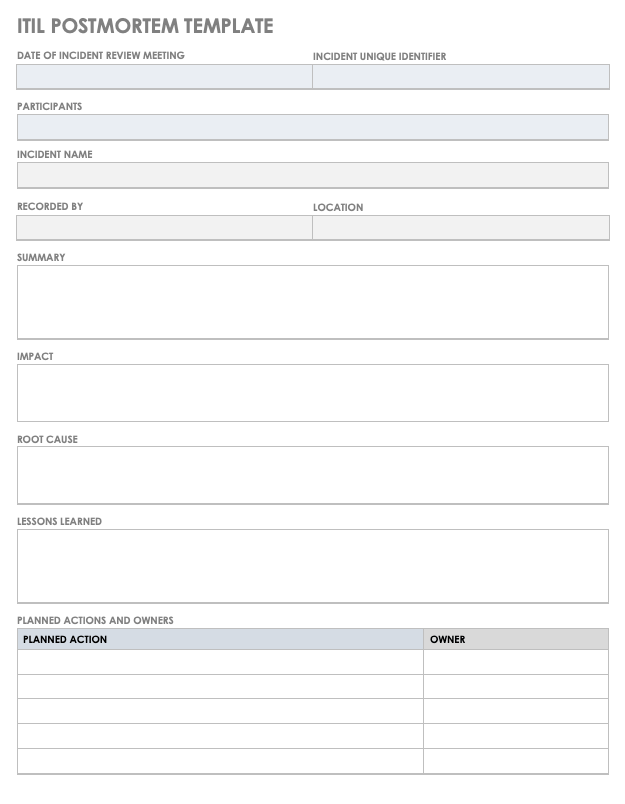
The incident template provides a comprehensive and precise account of the scenario, allowing management to make swift and informed decisions. It also aids within the recording of any incidences which may be necessary throughout company audit processes and even customer conferences. When it involves dealing with incidents, the ITIL framework, namely incident and downside administration, is essential.
Shopify was founded in 2006 by Tobias Lütke and Scott Lake after trying to open Snowdevil, an online retailer for snowboarding tools. Dissatisfied with the existing e-commerce products on the market, Lütke, a computer programmer by commerce, as a substitute built his personal. Lütke used the open supply web application framework Ruby on Rails to build Snowdevil’s on-line store and launched it after two months of growth.
Shopify’s software program can be used for in-person hashish gross sales in Ontario since becoming legal in 2019. In April 2017, Shopify introduced a Bluetooth enabled debit and credit card reader for brick and mortar retail purchases.
Firm
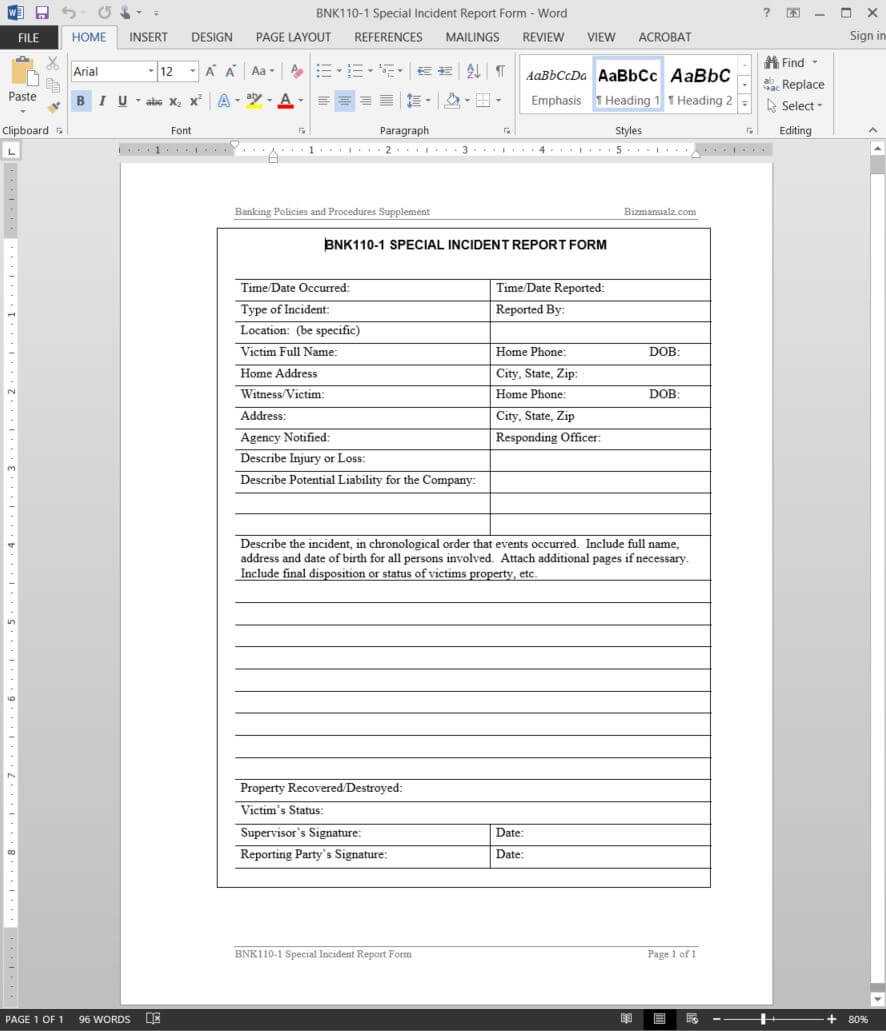
If the incident requires legal action, signed documentation will be needed to maneuver ahead with worker’s comp benefits or insurance claims. One of an important parts of a piece incident report is documenting who was concerned.

You have to spare template within the old style spot in the two substitute methods – catch the CustomSaveDialog occasion by deep gap ability and spare template in database within the CustomSavereport event. Depending on the type of breach, you may need only 3 days to notify end-users. This signifies that your preliminary detection team may solely have a couple of hours to begin the escalation process so that your company can examine, determine the full diploma of breach, and begin notifications.
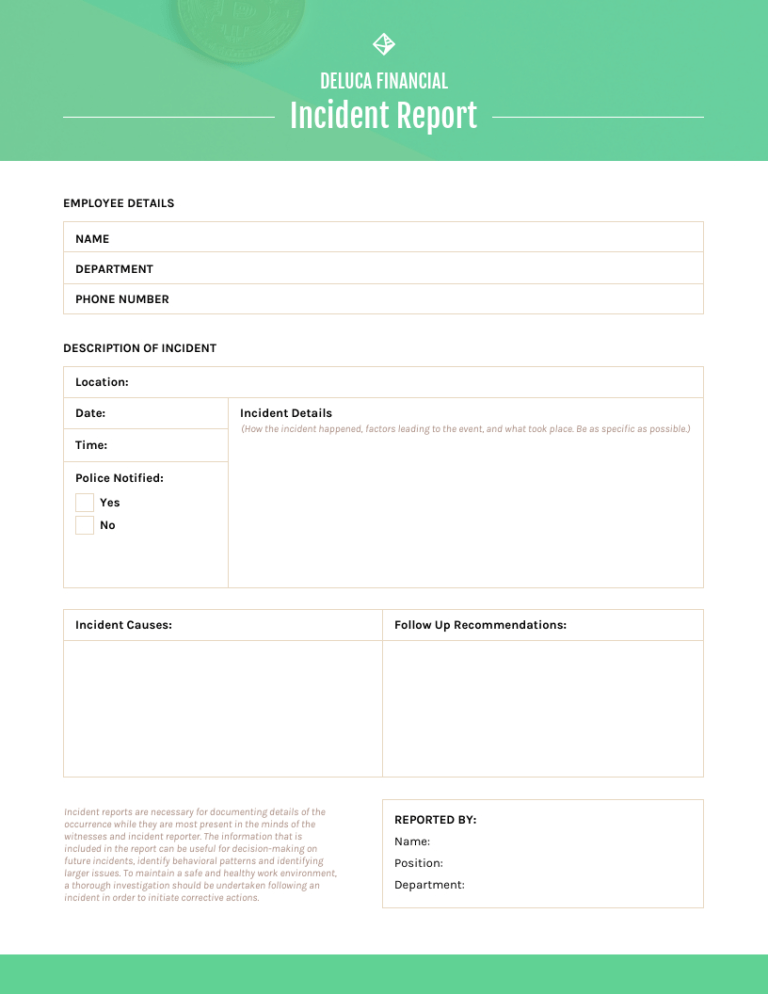
It’s additionally equally necessary to have a report ready that lets you record every related aspect of the incident details–this is the essential first step within the incident reporting process. As with any document you create for your small business, it’s good apply to incorporate your branding into your incident reviews. Here are some examples of type of incident reports to assist you get began.
We will again up all databases used on the project on a daily basis so that we are ready to roll them back simply in case of incidents. Apart from automated scheduled backups, our team will introduce database backups earlier than all main changes. Although we rely closely on exams in our improvement workflow, we are going to test even modifications associated to database updates on the staging server previous to rolling them out on the manufacturing server.
One of crucial features of this is to doc and analyze any incident that occurs. Incident reviews are sometimes used in the workplace when issues go mistaken. It’s a nice way to assist people perceive the severity of the difficulty and to avoid future errors.
Find out in case your group already has a process for writing an incident report letter. In many instances, organizations have a template for this type of letter and it’s best to comply with the supplied define to keep away from any inconsistencies. An incident report letter is a formal document that incorporates all the knowledge with regard to the actual occurrence that is being reported.
It helps document precise or potential injuries, unsafe circumstances on campus which will have contributed to the incident, whether or not bullying or harassment was concerned, and any disciplinary actions to be taken. This kind may be included as a part of a student’s everlasting document.
The third part of the document is the corrective motion that you just intend to take to avoid the security incident report template. This part contains information relating to security threats that have been detected and the procedures and measures that you have got taken to combat such security threats.

Do not copy and paste malicious code immediately into this type. Then, provide the resulting CISA Incident ID number in the Open Incident ID area of theMalware Analysis Submission Formwhere you presumably can submit a file containing the malicious code. A police incident report is a sort of incident report that is used to maintain monitor of the thefts/losses and any other forms of safety occasions that take place within specific premises.
The once a year report that every issue is required to kind out is key to the initiation of the organization. This report allows purchasers to understand how the presidency is getting alongside simply as the proceed and points which have occurred persistently. Every the extra significantly, it furnishes partners and speculators subsequent to a diagram of what’s going upon in a business.

This analysis helps reveal flaws in the software program system in addition to within the team’s actions or abilities in order that they’ll make improvements and prevent similar incidents in future. Though any incident is unpleasant, it’s greatest for teams to deal with incidents not as failures however as alternatives for enchancment. These examples of incident stories at the workplace are solely the tip of the iceberg when it comes to the variety of office accidents that can happen.

This can help to create a plan to prevent the same sort of incident from taking place again in the future. If a workplace vehicle was involved, all information about the vehicle ought to be noted, and the potential reasons why it occurred if there is no clear answer. This type permits each the employer and the company to keep a log of the injuries or illnesses that occur within the workplace.

Power and admin customers can then view all reports, and entry an extra form for responding to initial stories. Bug report form will assist you to to stay on prime of each scenario by accumulating real-time reviews about completely different issues which will come up with your on-line providers. The fifth section is the action that you just intend to take to improve the security of your system.
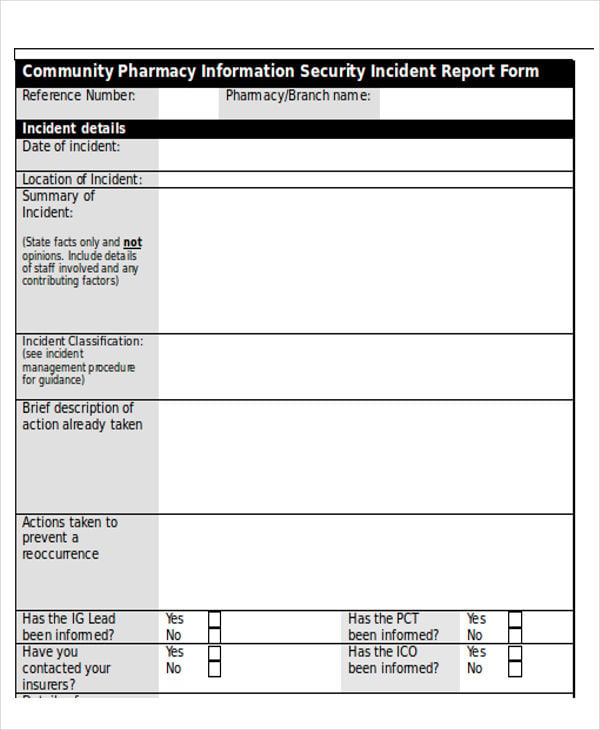
The knowledge breach incident report template can help your IT employees in logging the severity of safety breaches and creating a strategy to keep away from them sooner or later. It also helps hold monitor of something from knowledge breaches to privateness violations to viruses and denial-of-service assaults.

If one thing occurs in your office, it is your accountability to document it appropriately and do your half to verify it doesn’t happen once more. Device Magic allows you to simply create customized incident stories on your cellular gadgets, which may be completed within the field and store knowledge for simple sharing. The next time an incident occurs in your business, be ready.
By supplementing manual incident response with automated playbooks, organizations can cut back the burden on security groups, and reply to many extra security incidents, faster and more successfully. When constructing your incident response plan, it’s much easier to begin out with a template, take away components that are much less related on your organization, and fill in your details and processes. Below are a number of templates you can obtain for free, which may give you a head start.

By 2014, the platform had hosted roughly one hundred twenty,000 on-line retailers, and was listed as #3 in Deloitte’s Fast50 in Canada, in addition to #7 in Deloitte’s Fast 500 of North America. Shopify earned $105 million in revenue in 2014, twice as much as it raised the earlier 12 months.
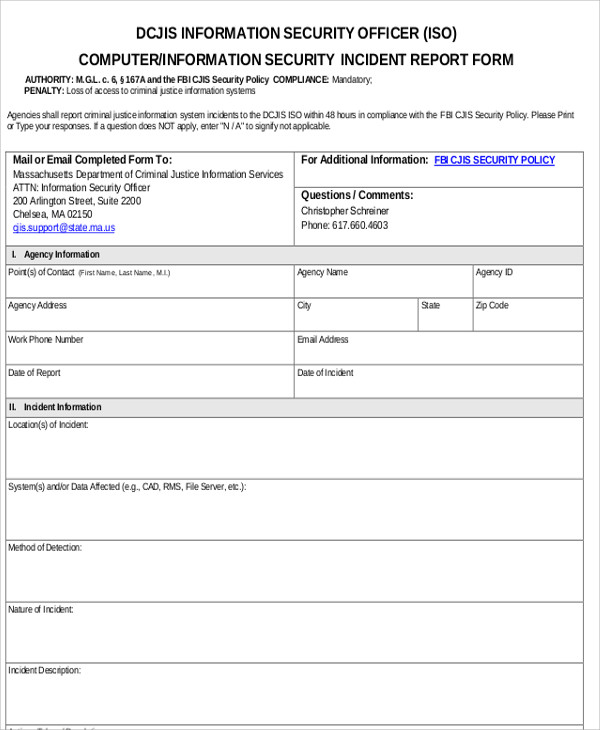
If an accident leaves an employee unable to work, correct reporting and documentation of the accident may be required for them to begin accumulating advantages. In this part, software development groups need to list all measures that must be taken to prevent similar incidents in future. These measures may include any necessary improvements to the project, improvement procedures, DevOps circulate, and so on.
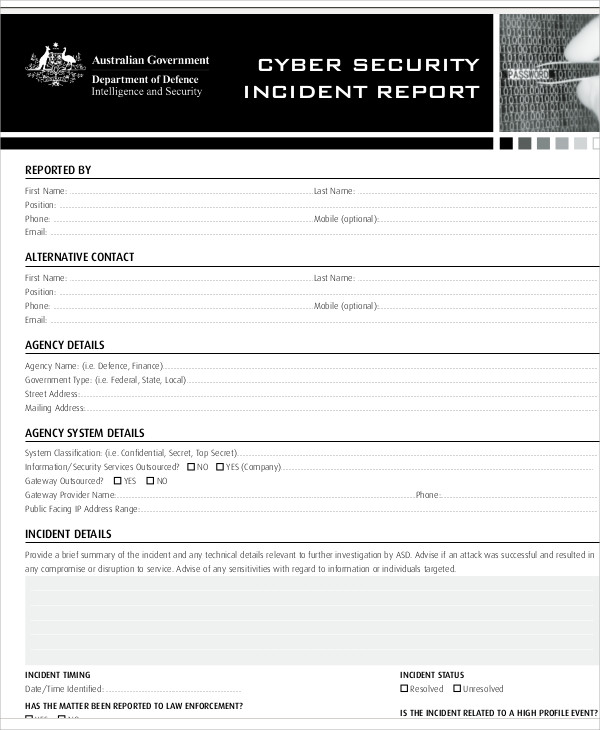
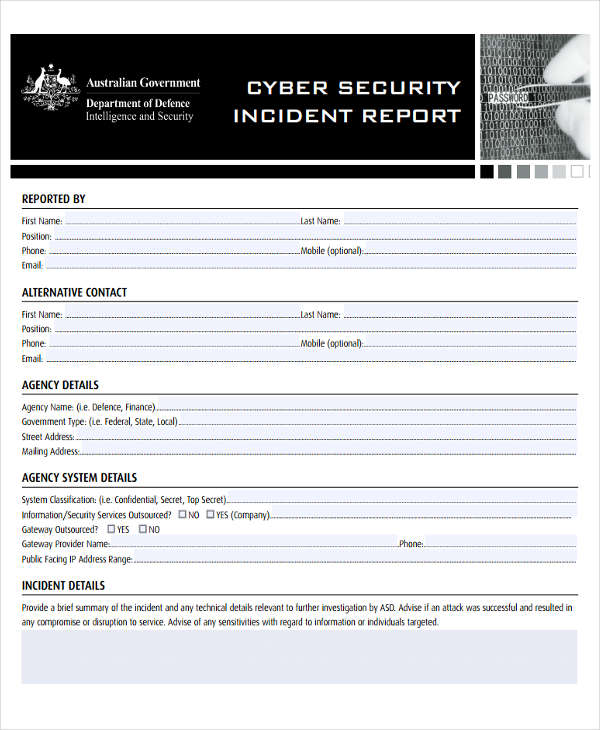
The report should embrace the person affected, a description of the incident, and any concerned events or witnesses. Please use this type to report a computer security incident. This kind can be utilized to report precise and/or suspected incidents that affect UWM computers, networks, websites, servers or providers.

Annie did not feel like she would wish further medical assistance and agreed together with her supervisor that she would need two to 3 days off work to ensure the burn didn’t get irritated. If this safety latch was on the saw when Kyle used it, it might not have cut his hand, however quite, routinely shut off once it jolted.
For instance, as you edit an Excel spreadsheet, every thing in the spreadsheet and all of your current adjustments are stored in RAM. If Excel suddenly crashed before you saved the document to your exhausting drive, you would still have a duplicate of your doc in RAM till one thing else overwrites it, or you turn off your computer. If you turn off a device, all working reminiscence is cleared as the RAM loses electrical present.

It is generally the first step in resolving a problem or issue that a customer, staff, or organization encounters. A written record of a problem or incidence that has been acknowledged, investigated, and resolved is recognized as an incident report.

Otherwise, if the incident occurred between Noon and Midnight, choose the “PM” box. The telephone number the place the Filer may be contacted to discuss the incident further ought to be produced on the line holding the “Phone” label.

Furthermore, Sheen is enthusiastic about providing insights to global clients on how technology can help them to do one of the best work of their lives. Get signatures earlier than completion – getting signatures from the affected individuals and witnesses confirms that the incident report is undoubtedly true. When Harvey fell, his colleague, Nick, who’s about to enter the warehouse, heard a close-by bang that urges him to verify what occurred.
- Ideally, this log system might be firewalled from the rest of the community and just a few very trusted people have access to it.
- The last phase of the template has a freshen for added conversations and for report entries.
- Report incident details and supporting system logs, audit data, and so on. to CIRT.
- To help tackle this downside, the security trade is creating tools to perform automated incident response.
- Typeforms are completely customizable and have tons of query types, allowing you to capture essentially the most relevant info, and replace your form based on what folks report.
- The report ought to embrace the person affected, an outline of the incident, and any involved parties or witnesses.
Network configuration, loading software program onto systems, and restoring backups is subsequent. Then they take a look at the flexibility of a ‘regular user’ to observe instructions to join to the new servers.

If not, you might be caught troubleshooting VPNs, firewall guidelines, and VLANs, and altering settings as your users complain. You can also be thinking about security incident response instruments.